HSM Mode - Hardware Security Module#
"HSM Mode" is the name we use when speaking about the Coldcard signing transactions without a person physically present. It's an advanced feature which requires additional software to setup and enable.
Not Supported on COLDCARD Q#
For HSM mode, the Mk4 can do everything the Q can do, since the QR scanner and other Q-related improvements are wasted in unattended mode. To make room for larger fonts and other features, HSM features are not provided on the Q.
CKBunker#
CKBunker is a helper program that makes it easy to reach your Coldcard over the Tor Network, and remotely submit PSBT files for signing. It also handles setup and configuration of the Coldcard's HSM features.
Learn more about CKBunker and read it's docs online, but first it may be helpful to understand Coldcard's HSM features.
You do not have to use CKBunker to make use of Coldcard's HSM features, and we expect other helper-programs to evolve in time.
Entering HSM Mode#
HSM mode can be enabled after a "policy file" has been uploaded and confirmed by the user. That policy file establishes what the Coldcard will and won't do in HSM mode, and what further authorization steps may be needed for each spending operation.
Once the Coldcard has gone into "HSM Mode", it must be powered-down before it can operate normally again. When a Coldcard has an HSM policy file already installed, you are given an opportunity to enable it each time the Coldcard is powered, just after the master PIN is entered and before the USB connection is enabled. It is also available in the main menu, as "Start HSM Mode".
When in HSM Mode, the Coldcard screen will look like this:
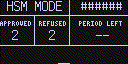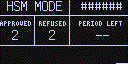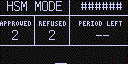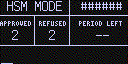
No transaction information is shown on the screen, although a progress bar and one-word description of current activity (ie. "Signing...") is shown along the bottom of the screen.
Important
Your funds in the Coldcard will only be as safe as your HSM Policy allows! We recommend a very low velocity (1BTC/day) and a whitelist of only one or two addresses.
Design your policy working from the assumption the attached computer may be compromised someday.
Further Reading#
- User Management: passwords and 2FA codes implemented in Coldcard.
- HSM Policy Rules: how much can be moved, where, and authorized by whom.
- Local Confirmation Codes: local user interactions at the Coldcard's location.
- Security Notes: understand our security model and related thinking.
For Implementors#
- USB Protocol support for HSM features
- CLI Usage examples: for use without the CKBunker.